💡 Unlock Cybersecurity Excellence at Just $599 per Module! 🌐
Revolutionize your cybersecurity strategy with our Dockerized Python code modules, now available at an unbeatable price of $599 per module. Empower your organization with cutting-edge tools designed to fortify your defenses, detect threats, and optimize diagnostics.
🚀 Key Features at Your Fingertips:
- Seamless Integration
- Advanced Threat Detection
- Scalability
- Comprehensive Diagnostics
- Automated Response
- Continuous Updates
- Developer-Friendly
- Performance Metrics
- Global Support
🔒 Why Choose Us?
- Affordability: Unleash the power of top-tier cybersecurity without breaking the bank. Our modules are priced at just $599 each, making excellence accessible to all.
- Flexibility: Customize your order with modules that align with your specific needs. With modular pricing, you have the flexibility to tailor your cybersecurity strategy according to your vision and scenario.
- ROI-driven: Our modules are not just an expense; they are an investment in the security and resilience of your organization. Experience a high return on investment with our cost-effective solution.
🛠️ How to Customize Your Order:
- Explore our Dockerized Python code modules.
- Choose the modules that best suit your cybersecurity goals.
- Tailor your order to match your unique vision and scenario.
- Enjoy instant access to enhanced security at an unbeatable price of $599 per module.
- Elevate your organization’s cybersecurity posture and stay ahead of evolving threats.
📈 Secure Your Future Today! Don’t compromise on cybersecurity. Invest wisely, invest in excellence. Secure your organization’s future with our Dockerized Python code modules – because robust cybersecurity shouldn’t be a luxury, it should be a standard.
Below is a simple example of a Python script that simulates a basic penetration test scenario. This script attempts to connect to a target server on a specified port and checks for potential vulnerabilities using a simulated exploit.
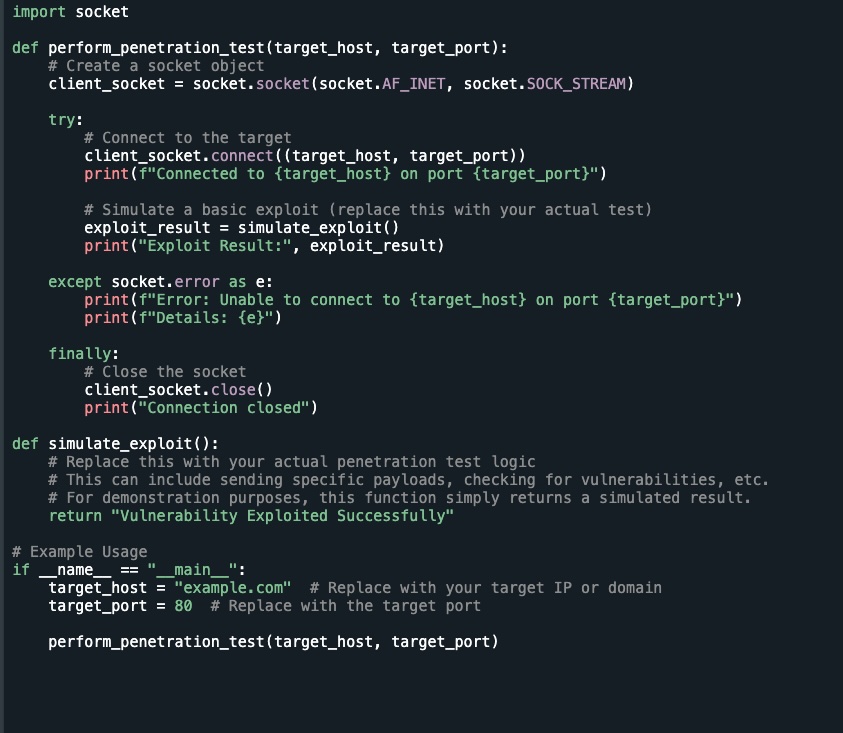
This script creates a socket connection to a specified target and port. It then simulates an exploit by calling the simulate_exploit() function. In a real-world scenario, the simulate_exploit() function would contain your actual penetration testing logic, such as sending specific payloads or checking for known vulnerabilities.
Remember, it’s crucial to have explicit authorization before conducting any penetration testing activities, and the script above is just a basic example for educational purposes.